
Yes, you will lose your Information!
The ILM2.0 reference model contains valuable reference information and practice methodologies and is a collaborative site where Information Lifecycle Management practitioners can participate in defining and promoting ILM2.0 best practices. Join the ILM2.0 Community. Our domain name search tool lets you search for domain names, domain extensions, and domains for sale at the same time. Results appear instantly.
Yes, you will lose your Information!
The ILM2.0 reference model contains valuable reference information and practice methodologies and is a collaborative site where Information Lifecycle Management practitioners can participate in defining and promoting ILM2.0 best practices. Join the ILM2.0 Community. Our domain name search tool lets you search for domain names, domain extensions, and domains for sale at the same time. Results appear instantly.
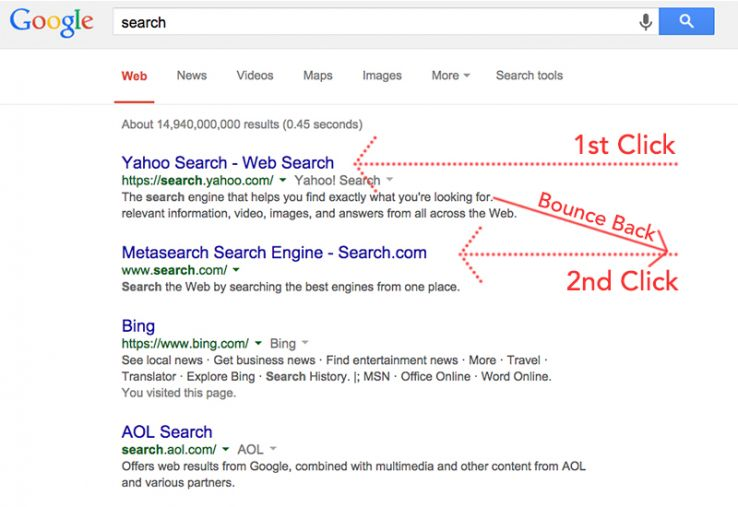
See Searches
An email address search provides an available email owner's name and social profiles. This is a useful search for understanding more about an email address to protect yourself from email scams, or to simply append your contact list. The search engine that helps you find exactly what you're looking for. Find the most relevant information, video, images, and answers from all across the Web. Alzheimer's and dementia research – find the latest information on research funding, grants, clinical trials and global research news.
Its easier than you think. Ever save something then not be able to find it again. In the digital preservation world, we have hit the wall. There is just too much information. Loss is inevitable. The question then, is not if, or when, but how much? And in the world of 'how much,' I choose to identify my critical information assets and make sure those are safe, secure, protected, and under my control not someone else's.
Top reasons for information loss:
- Poor Storage Practices:
- Millions of distributed files, many machines, external disk drives, external media, cloud storage services and no way to manage all this data as information assets.
- Which media has my file, is the file or the media corrupted, can I read it, can I interpret it, can I even get to it if it is in the cloud? etc…
- Poor Document Control Practices:
- Many versions, many backups, multiple cloud services, multiple devices, no index of files and locations
- Where is it, where is the master, who has it, how do I find it, how do I know this is the master file, what version is this one? etc…
- Loss of authenticity, loss of chain of control, inability to determine changes
- Poor Security Practices:
- Security breaches, hacking, spam, virus attacks, malware, loss of privacy, loss of confidentiality, identity theft, ransomware, information theft, intentional damage or changes, changed passwords
- Anything attached to the network or the internet is at risk of a security breach.
- Exposure or theft of personally identifiable information
- Human or Operational Errors:
- Failure to make redundant copies, to backup and test the restoration capability of your system regularly
- Failure to migrate files as operating systems, file systems, interfaces, media types, interfaces, etc. change
- Choosing unreliable storage systems or cloud service providers
- Failing to protect systems and storage from hackers or prying eyes
- Loosing control of the master and versions
Solve all of these and you will have a full-time job on your hands. There has to be a better way! And, there is…
See Search Ranking
About & Contact
|

